May 5, 2008 Comments Off on Cyber-Voyeurism: Social Data Browsing as Art
Cyber-Voyeurism: Social Data Browsing as Art
It’s arguable that most people, when posting to a personal blog or online forum, don’t expect the whole world to read their posts. Sure, they may know that what they’re writing is technically accessible to anyone with Internet access, but why would anyone be interested? It’s a little like carrying on a private conversation in line at the grocery store; you know you’re in public, and maybe a couple people will overhear you, but you don’t expect it to be recorded and broadcast on the News At Six.
Most of the time, our certainty of our own uninterestingness is warranted, but there are a few applications on the Internet that demonstrate how our “private” public information can be aggregated and cross-sectioned to make it truly public.
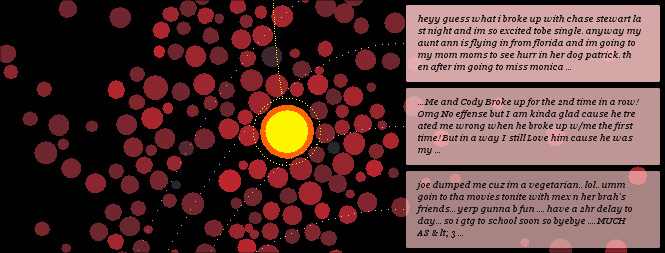 Take, for instance, The Dumpster. By using custom software to scan the Internet for the phrases “broke up” or “dumped me,” The Dumpster aggregated 20,000 posts – never intended to be seen outside the circle of friends or cybercommunity to whom they were originally posted – that constitute examples of teens in the aftermath of a breakup (according to the artists, “At least half of the authors of these breakups were American teenagers between the ages of 13 and 19. Approxmately seventy percent of the breakup authors were identified as female, while roughly fifteen percent were identified as male”). The artists’ statement indicates a number of reasons for launching the project, voyeurism chief among them.
Take, for instance, The Dumpster. By using custom software to scan the Internet for the phrases “broke up” or “dumped me,” The Dumpster aggregated 20,000 posts – never intended to be seen outside the circle of friends or cybercommunity to whom they were originally posted – that constitute examples of teens in the aftermath of a breakup (according to the artists, “At least half of the authors of these breakups were American teenagers between the ages of 13 and 19. Approxmately seventy percent of the breakup authors were identified as female, while roughly fifteen percent were identified as male”). The artists’ statement indicates a number of reasons for launching the project, voyeurism chief among them.
 Similarly, We Feel Fine scans the Internet on a continuous basis, looking for expressions of emotion. By accessing the profile information on the blogs it accesses, it’s able to sort the information it presents by age, gender, location, date, or even the weather outside when the post was written. We Feel Fine can isolate all the posts made by men who wrote about feeling horny when it was rainy, such as the 31 year old male in London, England who wrote, “i love my gym because most gyms are full of very fit people who make you feel slightly horny and quite inferior.” Probably he didn’t know when he wrote that that it would one day become part of an online art installation. There are a few different interfaces, including one that shows only images.
Similarly, We Feel Fine scans the Internet on a continuous basis, looking for expressions of emotion. By accessing the profile information on the blogs it accesses, it’s able to sort the information it presents by age, gender, location, date, or even the weather outside when the post was written. We Feel Fine can isolate all the posts made by men who wrote about feeling horny when it was rainy, such as the 31 year old male in London, England who wrote, “i love my gym because most gyms are full of very fit people who make you feel slightly horny and quite inferior.” Probably he didn’t know when he wrote that that it would one day become part of an online art installation. There are a few different interfaces, including one that shows only images.
 Digging into even more personal territory is I Want You To Want Me, an installation commissioned by the MoMA for Valentine’s Day 2008. It uses balloons to visualise data gleaned from online dating profiles. Like the randomly interactive nature of the last two examples, I Want You To Want Me lets viewers browse the information presented in 5 “movements” which display balloons based on a given modality, whether it’s what the person who wrote the profile wants, how they see themselves, or even a matchmaker mode which pairs two profiles based on algorithmically determined compatibility.
Digging into even more personal territory is I Want You To Want Me, an installation commissioned by the MoMA for Valentine’s Day 2008. It uses balloons to visualise data gleaned from online dating profiles. Like the randomly interactive nature of the last two examples, I Want You To Want Me lets viewers browse the information presented in 5 “movements” which display balloons based on a given modality, whether it’s what the person who wrote the profile wants, how they see themselves, or even a matchmaker mode which pairs two profiles based on algorithmically determined compatibility.
The commonalities between these three visualisations for viewing social data say a lot about the underlying motivations for social data browsing. Given a choice of aggregating any type of information on the Internet, all three groups artists immediately went for the intensely personal – whether it’s the self we construct when looking for a mate, the trauma of a breakup, or simply the emotions we choose to express. The voyeuristic intent of all three projects is transparent. These works present an interesting juxtaposition, one that directly plays on our perceptions of privacy on the Internet; it’s important to note that all three visualisations have withheld the authors’ (screen)name and any identifying information, but nonetheless the thrill of all three works comes from the friction between the original authors’ intentions for their posts and the artists’.
The subject of privacy on the Internet is something I intend to write about at greater length in the future, but for now, I will merely highlight the fact that something like social data browsing (or cyber-voyeurism in general) is dependent on the fact that our sense of privacy in what we do online is misplaced.
A final note on cyber-voyerism, one that goes a step beyond aggregating online social data posted in public blogs and forums: as reported by Wired.com, even pictures and writings we post online which are not available to the public are susceptible to theft and rebroadcast. Myspace.com allows users to post profiles featuring public pictures and notes, but also to post pictures and notes which remain accessible only to friends approved by the poster. The pictures, theoretically, require permission before they can be viewed. But last January a hacker known as DMaul hacked into Myspace to access and copy 44,000 profiles, and reposted them online, available for downloading.
There’s a certain similarity to the three art projects and DMaul’s file – people who posted things expecting only a handful of known acquaintances to access them suddenly find their information collected and reposted for the entire world to see – but there’s an important qualitative difference. Even though they were posted online with the expectation of a minimal audience, the fact remains that the information aggregated in the first three examples was always totally available to the public. As such, there can be no reasonable expectation of privacy. The Myspace posters, on the other hand, did have a reasonable expectation of privacy, Myspace’s disclaimers notwithstanding. The posters in the social data visualisations may feel violated, but whatever rights to privacy they may have felt they had, they waived when they posted in a forum accessible by anyone.
To wit: the right to privacy and the expectation of privacy are two totally different things. This is something understood not only by the artists, but by the viewer as well – because the frisson of voyeurism depends on the subject’s lack of complicity (therein lies the distinction between voyeurism and exhibitionism). While the posters may or may not have known that once they posted something online, their right to privacy over an image or bit of text vanished, it’s a given that they understood their privacy to be secure from a practical, de facto point of view. It serves as a curious illustration that a significant gap lies between our perception of online privacy and the fact of it.